Difficulty —Medium
In this challenge, we are given a zipped ransomware and the encrypted flag. Our objective is to reverse engineer the ransomware to find how the flag is encrypted to decrypt the flag.
I started my analysis by importing the ransomware into Ghidra
Encrypt Function
When looked at main function, I saw interesting function — encrypt
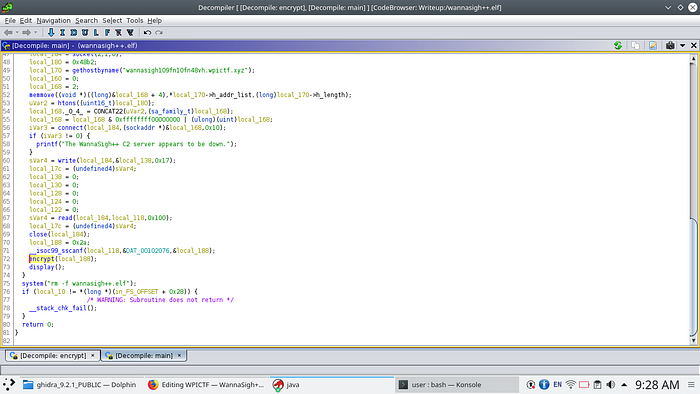

From the de-compiled code in ghidra i understood that the ransomed flag is created by XORing the flag with random integers generated with a seed which is given as parameter for the function.
I started hunt to find how the how the seed is generated. So, Back to main function
Next function i found interesting was getIPStr Function
getIPStr Function

It uses curl to send a request to https://bot.whatismyipaddress.com to retrieve your IPv4 address and saves it to memory.
On further analysis of the main function, I understood that ransomware send something to a remote address(wannasigh109fn10fn48vh.wpictf.xyz) on the port 0x48b2 or 18610.
so I used net cat to figure out what it retrieves from the server

That gave a back a message. So that was not something i was supposed send.
After sometime i figured out that my IPv4 is concatenated with the string ‘Baahhhh_’ so the whole string becomes ‘Baahhhh_IPv4’

And that is int also the seed for our encrypt function
And i used a simple python script to decrypt the flag

Flag : WPI{backup-your-files}